Nimble Streamer supports variety of features for HLS, including big feature set for live streaming. In order for HLS to support secure streaming, the initial HLS RFC has a description of protection mechanism based on AES-128 encryption. This allows covering Digital Right Management (DRM) use cases.
Nimble Streamer has now encryption support. It allows encrypting chunks using DRM key specified by server admin. It supports the following key scenarios
Let's review each scenario separately. We assume that your system administrator has already installed and set up Nimble Streamer and it has streams ready to be protected by DRM.
Note, that Nimble Streamer encrypts only self-produced HLS streams, those can be VOD streams or transmuxed Live streams. Therefore, HLS encryption can't be applied to re-streaming scenarios.
In this scenario the DRM AES-128 encryption key is provided by Nimble itself. Let's go step by step to see how it is set up and used.
The whole scenario is shown on the following sequence diagram.
Server administrator goes to Control top menu and selects HLS AES encryption DRM.
This opens a dialog shown below.
The DRM key field has the key used for further DRM encryption. You may re-generate the key any time. Clicking Save brings the value to the Nimble Streamer instance.
When the visitor wants to play the media, the player requests a stream playlist from Nimble Streamer. The playlist is returned with chunk-list (nested playlist), which content is similar to the one listed below.
The player downloads the key and starts requesting chunks.
When Nimble gets the request for a chunk from player, that chunk is being encrypted by AES-128 using the assigned encryption key. Then it's being returned to the player.
Player gets the chunk and decrypts the content with previously downloaded key.
Further workflow is based on the same steps - chunks are requested and processed with the key obtained from the URL hosted by Nimble.
This scenario is similar to the scenario 1, the difference is that the DRM AES-128 encryption key is provided by the external handler.
This scenario is shown on the sequence diagram below.
Here are the steps to follow.
As in scenario 1, server administrator goes to Servers menu, selects Nimble Streamer instance and clicks on DRM Setup.
This opens a dialog shown below.
The DRM key field has the key used for further DRM encryption. You may re-generate the key any time.
To specify a URL for external key handler click on "I also want to use my own DRM key URL" to see additional field.
Enter the DRM URL where the key will be obtained. Clicking Save brings the value to the Nimble Streamer instance.
If the key DRM URL is specified, Nimble Streamer will not be returning the key like described in step 1.2. So you need to implement the functionality which will return the correct key, see step 2.2.
The DRM URL specified at step 2.1 must point to the location of the handler which is responsible for returning DRM key. Typically it's a web application which makes decision whether a viewer may get the DRM key or not.
The returned key must be the same as the key specified in DRM key field at step 2.1.
The Content-Type of the returned key must be application/octet-stream. The key itself needs to have binary format according to HLS RFC mentioned in the beginning of this article.
If a WMSAuth signature is used for authenticating a user, this parameter is also passed to the handler. So you may implement pay-per-view system based on DRM encryption.
When the visitor wants to play the media, the player requests a stream playlist from Nimble Streamer. The playlist is returned with chunk-list (nested playlist), which content is similar to the one listed below.
The player obtains the key from the handler and starts requesting chunks.
Just as in step 1.3, when Nimble gets the request for a chunk from player, that chunk is being encrypted by AES-128 using the assigned encryption key. Then it's being returned to the player.
Player gets the chunk and de-crypts the content with previously downloaded key.
Further workflow is based on the same steps - chunks are requested and processed with the key obtained from the handler URL.
Also take a look at Nimble Streamer DRM feature set which covers various encryption.
Nimble Streamer, Nimble Streamer DRM, HLS RFC, Nimble Streamer HLS support for VOD streaming, WMSPanel Paywall framework, SSL support for HTTP streaming in Nimble Streamer, Verimatrix VCAS DRM support in Nimble
Nimble Streamer has now encryption support. It allows encrypting chunks using DRM key specified by server admin. It supports the following key scenarios
- Nimble hosts the key URL and uses it for giving out the key.
- External key URL is used for the cases when a customer needs additional authentication for a key.
Let's review each scenario separately. We assume that your system administrator has already installed and set up Nimble Streamer and it has streams ready to be protected by DRM.
Note, that Nimble Streamer encrypts only self-produced HLS streams, those can be VOD streams or transmuxed Live streams. Therefore, HLS encryption can't be applied to re-streaming scenarios.
1. Using encryption key hosted by Nimble
The whole scenario is shown on the following sequence diagram.
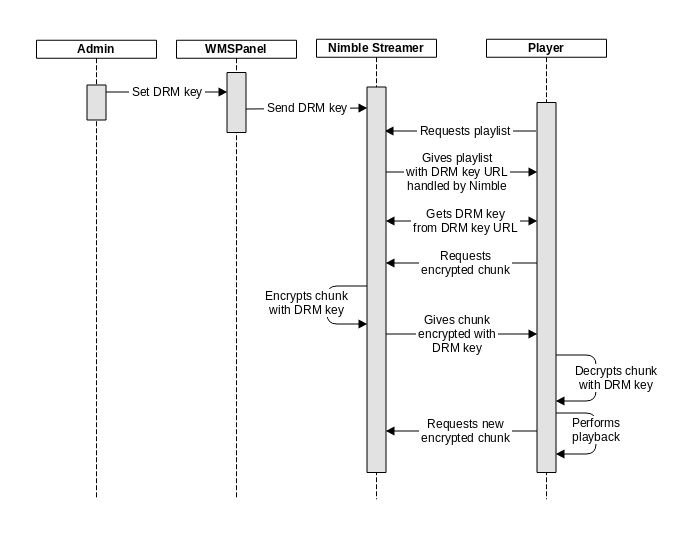 |
| AES DRM encryption workflow with Nimble Streamer hosting the DRM key. |
1.1 DRM key setup
Server administrator goes to Control top menu and selects HLS AES encryption DRM.
This opens a dialog shown below.
The DRM key field has the key used for further DRM encryption. You may re-generate the key any time. Clicking Save brings the value to the Nimble Streamer instance.
1.2 Playlist and key exchange
When the visitor wants to play the media, the player requests a stream playlist from Nimble Streamer. The playlist is returned with chunk-list (nested playlist), which content is similar to the one listed below.
#EXTM3UIn EXT-X-KEY field you may see the URI which is used for returning the encryption key assigned at step 1.1. This URI is hosted by Nimble instance itself.
#EXT-X-VERSION:3
#EXT-X-TARGETDURATION:10
#EXT-X-MEDIA-SEQUENCE:0
#EXT-X-KEY:METHOD=AES-128,URI="hls.key?nimblesessionid=5"
#EXTINF:3.75,
n_0.ts?nimblesessionid=5
#EXTINF:7.5,
n_1.ts?nimblesessionid=5
#EXTINF:7.5,
n_2.ts?nimblesessionid=5
The player downloads the key and starts requesting chunks.
1.3 Chunks processing
When Nimble gets the request for a chunk from player, that chunk is being encrypted by AES-128 using the assigned encryption key. Then it's being returned to the player.
Player gets the chunk and decrypts the content with previously downloaded key.
Further workflow is based on the same steps - chunks are requested and processed with the key obtained from the URL hosted by Nimble.
2. Using encryption key from external URL
This scenario is similar to the scenario 1, the difference is that the DRM AES-128 encryption key is provided by the external handler.
This scenario is shown on the sequence diagram below.
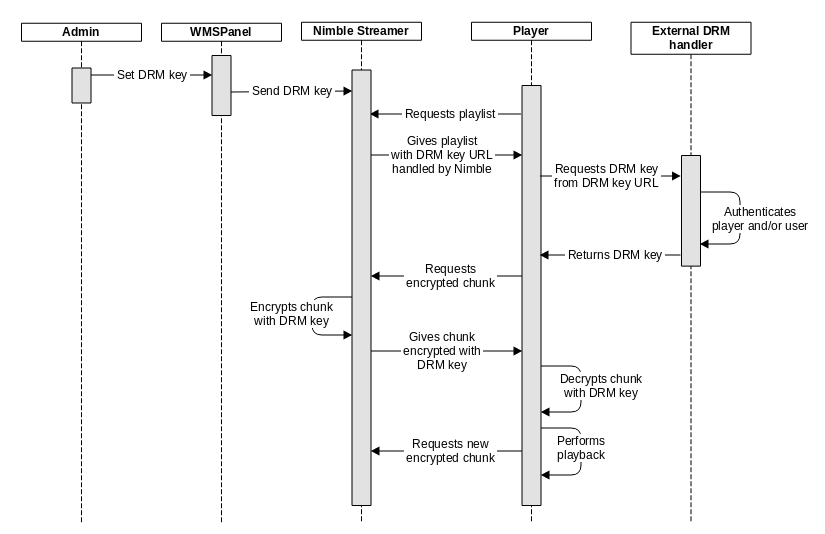 |
| AES DRM encryption workflow with external DRM key handler. |
Here are the steps to follow.
2.1 DRM key setup
As in scenario 1, server administrator goes to Servers menu, selects Nimble Streamer instance and clicks on DRM Setup.
This opens a dialog shown below.
The DRM key field has the key used for further DRM encryption. You may re-generate the key any time.
To specify a URL for external key handler click on "I also want to use my own DRM key URL" to see additional field.
Enter the DRM URL where the key will be obtained. Clicking Save brings the value to the Nimble Streamer instance.
If the key DRM URL is specified, Nimble Streamer will not be returning the key like described in step 1.2. So you need to implement the functionality which will return the correct key, see step 2.2.
2.2 DRM key URL handler
The DRM URL specified at step 2.1 must point to the location of the handler which is responsible for returning DRM key. Typically it's a web application which makes decision whether a viewer may get the DRM key or not.
The returned key must be the same as the key specified in DRM key field at step 2.1.
The Content-Type of the returned key must be application/octet-stream. The key itself needs to have binary format according to HLS RFC mentioned in the beginning of this article.
If a WMSAuth signature is used for authenticating a user, this parameter is also passed to the handler. So you may implement pay-per-view system based on DRM encryption.
2.3 Playlist and key exchange
When the visitor wants to play the media, the player requests a stream playlist from Nimble Streamer. The playlist is returned with chunk-list (nested playlist), which content is similar to the one listed below.
#EXTM3UIn EXT-X-KEY field you may see the URI which you set up at step 2.1.
#EXT-X-VERSION:3
#EXT-X-TARGETDURATION:10
#EXT-X-MEDIA-SEQUENCE:0
#EXT-X-KEY:METHOD=AES-128,URI="http://example.com/drm/hls.key?nimblesessionid=7"
#EXTINF:3.75,
n_0.ts?nimblesessionid=7
#EXTINF:7.5,
n_1.ts?nimblesessionid=7
#EXTINF:7.5,
n_2.ts?nimblesessionid=7
The player obtains the key from the handler and starts requesting chunks.
2.4 Chunks processing
Just as in step 1.3, when Nimble gets the request for a chunk from player, that chunk is being encrypted by AES-128 using the assigned encryption key. Then it's being returned to the player.
Player gets the chunk and de-crypts the content with previously downloaded key.
Further workflow is based on the same steps - chunks are requested and processed with the key obtained from the handler URL.
Also take a look at Nimble Streamer DRM feature set which covers various encryption.
Related documentation
Nimble Streamer, Nimble Streamer DRM, HLS RFC, Nimble Streamer HLS support for VOD streaming, WMSPanel Paywall framework, SSL support for HTTP streaming in Nimble Streamer, Verimatrix VCAS DRM support in Nimble


